One thing we have learned from the past few weeks is that although the cyber threats that businesses face have not changed significantly, the way in which attackers and workforces have adapted, have. We have seen attackers preying on the fears of internet users around the COVID-19 pandemic to help them achieve their aims, particularly those with a financial motivation, but also likely nation-state attackers.
We have also seen a workforce mobilised to work remotely more heavily than ever before. The same is likely true of many of the attackers, having impacts on the way they can work.
We have summarised the ways in which we expect to see the attackers adapt further and the changes we expect to see in the coming months.
Attackers will be impacted by local lockdowns and previous working environments
Our research shows a decrease in overall cyber-attack activity, with a specific increase in COVID-19- related attacks.
Many attackers will have always worked remotely online, such as many Russian and English-speaking cybercriminals, and lockdown may have minimal impact on their ability to conduct attacks and provide online services. These attackers have traditionally worked remotely, forming loose groups online. It is only more recently that more organised groups have been thought to work together in physical offices.
However, physical money-laundering (so-called “cashout”) from ATMs and banks will inevitably be affected due to the closure of some facilities and increased police scrutiny on the streets. This may lead to increased chances of financial recovery. Our experience of retrieving funds shows that we have a golden 24 hours in which to act, with easy recovery of funds diminishing over the next 30 days.
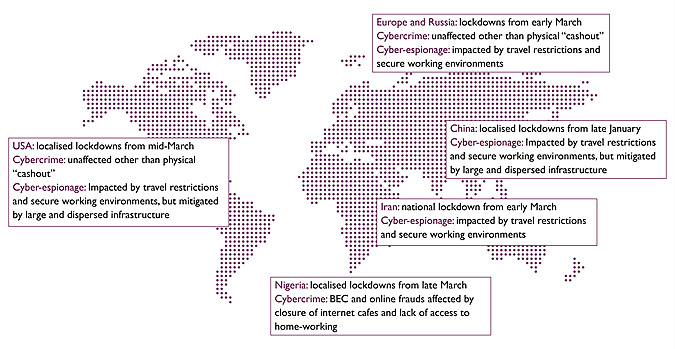
Business Email Compromises (BEC) frauds show no current signs of abating. We have seen threat groups in this area operate from Nigeria as well as other countries. Nigerian cyber-fraudsters may see an impact on their ability to “do business” with lockdowns imposed on the main cities and internet cafes likely to be closed, where some groups are known to operate.
It is also likely that regional lockdowns will have an impact on state-sponsored attackers who are working in highly physically-secure office environments. While these espionage groups may continue to conduct campaigns, we expect to see these decrease in intensity as lockdown policies and infection rates impact the ability of workers to get to these secure environments and restrict the number of staff in offices.
Not only that, but some tried and tested techniques, such as targeting events and hijacking, for example, hotel Wi-Fi sessions, is now all but impossible in many regions as business travel has abated. State sponsored attackers must now change targeting tactics to gather intelligence, likely focusing on countries with more relaxed lockdowns, or towards users working remotely in their homes.
In China and Iran, which saw early lockdowns and are known for cyber-espionage against Western nations, operations may have been impacted negatively. Iran faced a national lockdown, likely affecting espionage operations absolutely, but recently relaxed. China implemented regional lockdowns. Following significant military reorganisation of China’s capabilities in the past five or so years, military cyber centres are likely geographically dispersed across the country, meaning the effects of localised lockdowns in cities and provinces may have mitigated the impact. Although affected, Chinese espionage operations may have been able to continue at a reduced but regular pace with this resilience in place. We expect to see these regional variations reflected in future reporting of these attacks.
Attackers will continue to focus on video-conferencing, even after lockdowns ease
Life after the pandemic is beginning to gain attention, with politicians being pushed for exit strategies as economic pressures bite. It is unlikely that the world will return to normal quickly, and some aspects will be changed forever. We expect to see a higher user-base of video-conferencing and remote working persist even after the pandemic ends and lockdowns lift as users become accustomed to these practices. Necessity has overridden some of the previous resistance to stopping face to face meetings or the lack of trust often placed in remote workers over office-based staff.
The next three months will see heavy use of video-conferencing and collaboration applications. The use of video applications has now crossed a generational divide, although applications such as TikTok and Snapchat may still be largely limited to certain demographics. Most organisations are now using a combination of technologies which we are seeing targeted day by day.
The widespread use of these applications will require them to be bought into the security environment of the organisation. At present many applications don’t integrate well, and we expect to see vendors become more ‘corporate’.
We have been helping clients select secure conferencing solutions and developing an overall strategy for secure conferencing and collaboration. These strategies tend to involve picking a single solution, but often require purchasing other solutions in the short term in order to essentially lock users out from the vulnerable service.
These solutions are likely to become an attack vector in their own right if adoption stays high, with attackers using them as a mechanism to deliver phishing attacks as we have seen with other open access messaging solutions.
Ransomware will focus on healthcare, supply-chains and online services. Weakened industries may be more vulnerable
Ransomware and other extortion-driven cyber attacks have seen a resurgence in the last year. It is likely that this will continue, driven by reduced economic activity, increasing crime rates and technical vulnerabilities from a work force returning to the office.
We expect to see an increase in healthcare organisations being targeted, as well as critical supply chains, online retail and payment providers. Healthcare is likely to see a long tail to the pandemic, which will reduce their capability to manage cyber security whilst Government attention is also directed elsewhere.
Attackers need to maximise the pressure they can bring to bear in order to deliver a financial return. This may lead to a focus on economically weaker sectors such as Aviation, Hospitality and Leisure who have seen major headwinds. These sectors are likely to be reducing discretionary spend and transformation programmes including cyber security.
Policy changes could be on the horizon
Ultimately extortion exists anywhere where an attacker can reduce access or availability of a valuable resource. It is unlikely that these issues will be prevented without legislation preventing the payment of ransoms. A 'no ransom' policy has been the default position for the US Government in other areas such as terrorism, which shows some evidence of being effective against financially motivated attackers. The US OFAC also started imposing sanctions on ransomware bitcoin addresses in 2018, and similar strategies could be seen adopted more widely as part of regular enforcement efforts.
The New York State Senate has been presented with a bill that would restrict the use of taxpayer money to pay ransoms, alongside a fund for security improvements. The bill is intended to become active from January 1 2022, after which no ransom could be paid. If successful, it is possible that other local and national governments could follow suit resulting in a very different landscape for extortionists, who may switch targeting or methods in response.