On 11 September 2020, cybersecurity vendor Secura published details of CVE-2020-1472, a critical privilege escalation vulnerability present in Netlogon Remote Protocol (MS-NRPC). Secura refers to this vulnerability as "Zerologon". Successful exploitation of this vulnerability can allow an attacker to impersonate any machine within the network when authenticating against a domain controller (DC). Secura has demonstrated that this can be used to elevate privileges to Domain Administrator level, providing access across the entire network. The Zerologon vulnerability is likely to affect many organisations prior to patch rollout. Exploitation is expected imminently and businesses should prioritise deployment of the available patch released by Microsoft.
Overview
MS-NRPC is an authentication mechanism run on all Windows Servers which is used to authenticate users and services within a Windows Active Directory (AD). Microsoft has confirmed that this vulnerability impacts all Windows Server versions meaning that prior to patching, vulnerability will be present in all Windows AD environments. Microsoft released a patch for CVE-2020-1472 in 11 August 2020 but due to its severity did not publish any accompanying description of the vulnerability.
CVE-2020-1472 relates to a weakness in the cryptographic implementation underpinning the authentication handshake used for MS-NRPC. MS-NRPC uses a custom cryptographic protocol in which a client and server exchange random eight-byte nonces to compute a shared session key which is then used to compute a client credential. Secura determined that it is possible to craft an MS-NRPC authentication request which inserts a string of eight zeros as one of the values used to calculate the session key. As a known input is used, by submitting multiple authentication requests an attacker can force the session key generation process to generate a predictable output – a key consisting entirely of zeros. This process reportedly takes around three seconds to complete. To accomplish this an attacker would only need access to a single machine within the target network.
Capability to control session key generation can allow an attacker to successfully authenticate against the target server over MS-NRPC as any machine within the AD, including a DC. Moreover, it is possible to authenticate against a DC while also impersonating that DC. Successfully authentication can allow for a range of malicious actions, including changing the AD password of any machine on the network. While this does not change the password stored locally in registry on the target machine, Secura reportedly established that after changing a DC's AD password it was possible to use this credential dump Domain Administrator password hashes. These could then be used to conduct a Pass-the-Hash attack and log onto the target DC, gaining Domain Administrator privileges.
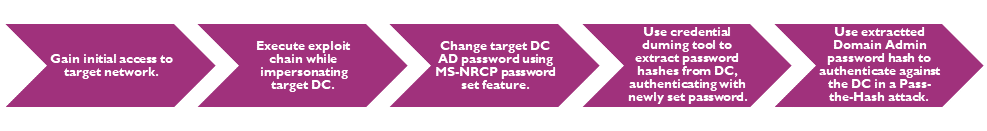
Figure 1 - Process for exploiting CVE-2020-1472 and gaining Domain Admin privileges.
Secura have not released any proof of concept (PoC) exploit code for CVE-2020-1472 but have released a Python script which can be used to test whether a server is vulnerable.
Assessment
As the only requirement for successful exploitation of CVE-2020-1472 is access to a single machine within the target network, the general methodology for gaining Domain Admin through exploitation of CVE-2020-1472 outlined by Secura is assessed to represent a substantial potential risk to organisations. Domain Admin privileges enable an attacker to access and control virtually any machine in the network, allowing for completion of a wide range of objectives. Exploits for this vulnerability would almost certainly be of use for achieving lateral movement and privilege escalation in any operational context.
Attackers seeking to maintain long term covert access to a network will often try to achieve this to help them maintain persistence and spread laterally. DCs are however also targets in short more impactful attacks – ransomware operators often attempt to gain Domain Admin privileges to enable them to run ransomware on every computer in a network.
MDR Cyber assesses that the method used by Secura to gain Domain Admin represents only one possible approach and that other operational implementations are highly likely viable. Mitigations based around the detection or blocking of specific tools and techniques used by Secura are therefore unlikely to be effective.
Threat forecast
Exploitation of this vulnerability had not been reported in the wild at the time of writing and no proof of concept (PoC) exploit code has been released. However, multiple credible security researchers have publicly claimed to have successfully modified the Python script published by Secura to achieve successful exploitation of CVE-2020-1472 against a DC. It is therefore assessed to be highly probable that a functional PoC exploit will be made public in the immediate to near-term future.
Additionally, due to the high impact nature of this vulnerability it is almost certain that this disclosure has led threat groups with exploit development capability to begin working to develop a functional exploit for CVE-2020-1472. As a legitimate security researcher has already claimed to have achieved exploitation in a test environment, exploitation in the wild is likely imminent.
Mitigation options
MDR Cyber recommends that organisations explore the following options to mitigate and detect exploitation of this vulnerability:
- Microsoft has released a patch to mitigate this vulnerability, details of which are available here. Organisations should expedite rolling out this patch to all Windows Servers within their network environments. No workarounds for this vulnerability have been identified.
- In addition to rolling out this patch, Microsoft advises enabling Domain Controller (DC) enforcement mode on all DCs as this prevents usage of the vulnerable cryptographic implementation. Microsoft has stated that this will be enforced from 09 February 2021. Guidance on this is available here.
- Microsoft has developed new Windows Event codes which can be used to track and detect both allowed and denied MS-NRPC connections using the vulnerable cryptographic implementation, further details available here. Monitoring for event IDs 5827, 5828, 5830, 5831, and 5829 can help to provide visibility of potentially vulnerable connections. Microsoft has published a PowerShell script which can be used to parse Windows Event Logs for these event IDs, available here.
- Operational use of exploits for CVE-2020-1472 revolves around obtaining and reusing high privilege credentials. An attacker's pathway to successful use of extracted credentials can be made more complex by implementing restrictions on which machines are able to initiate logons to a DC, forcing an attacker to first move laterally to access to one of these machines. Paired with heightened monitoring of logons to these machines and DCs this approach would provide a better chance of detecting use of credentials harvested through exploitation of CVE-2020-1472.
- The implementation chain outlined by Secura relied on use of a Pass-the-Hash attack against a target DC. While this will not detect alternative approaches, monitoring for the following Windows event IDs can help facilitate detection of Pass-the-Hash attacks:
Source host logs (i.e. the machine the attacker is operating from)
4648 – A logon was attempted using explicit credentials.
4624 – An account was successfully logged on (Logon type 9).
4672 – Special privileges assigned to new logon.
Target host logs (i.e. the machine the attacker is trying to run commands on)
4624 – An account was successfully logged on (Logon Type 3).
4672 – Special privileges assigned to new logon.
Domain controller logs
4776 – The computer attempted to validate the credentials for an account.