Beware WhatsApp messages asking you to urgently send them a code, even those from your contacts.
With the COVID-19 pandemic resulting in people having to stay connected to family and friends through social media and mobile devices, WhatsApp has seen a 40 per cent increase in usage. In some countries, this number was much higher; Spain experienced a 76 per cent increase in time spent on the messaging app during the early phases of lockdown.
It is unsurprising, therefore, that financially-motivated cybercriminals are increasingly targeting the app and its users. A year-old attack has resurfaced and MDR Cyber have seen a surge in cases globally since March. A brief Twitter analysis reveals hundreds of tweets from users claiming to have had their accounts compromised after supposedly being messaged by someone they know.
How it works
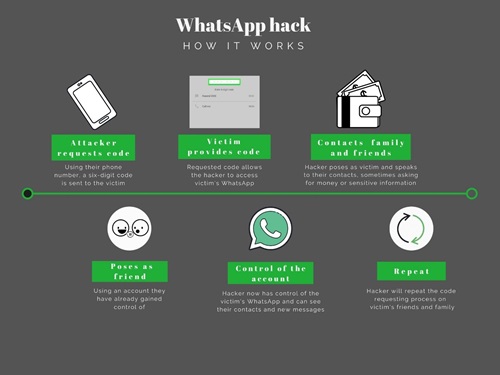
Initially, the attacker will use a target victim's number to request an account reset. This results in a six-digit code being sent via SMS to the target's phone.
The attacker will typically then pose as the victim's friend by using a WhatsApp account they have already hijacked. They tell their victim that they are having issues receiving a six-digit code, and have sent it to their number instead. This code is the one-time passcode needed to install WhatsApp on a new phone, and when the victim sends it back to the attacker, they can then access their account.
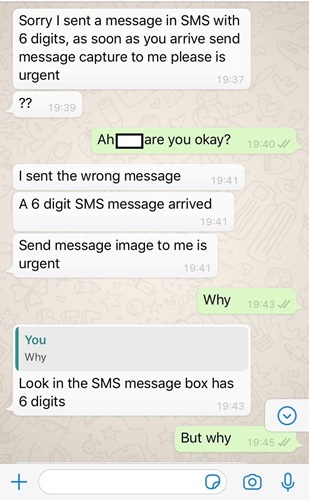
Figure 1: A scammer using an already compromised account to try and repeat the process
With access to the hijacked account, the attacker can see the victim's contacts, new messages and WhatsApp groups. It also effectively locks out the true owner of the account from their current phone.
Attacker motivations
Once the attacker has control, they may use it to message other friends asking for money, claiming an emergency, or may trick them into sharing their bank account details. The attacker will then repeat this process on more of the victim's friends and WhatsApp contacts.
This attack is particularly effective because the attacker contacts their victim from the legitimate account of someone they know. This is a classic example of social engineering whereby attackers use deception to manipulate individuals' behaviour.
Exploiting the relationship between the new victim and the person whose account the attacker is using is key to success and is difficult for many users to spot. A person is more likely to divulge personal and sensitive information to someone they know and trust which is why this method has the potential to be very profitable for the attacker.
The attackers
It is unclear from current reporting who the attackers behind this attack are, although from the syntax of the various messages we have reviewed, it is unlikely that their first language is English (Figure 2). It is possible that, given the unsophisticated nature of the operation, multiple separate groups or individuals are running the same scam.
Anyone with a WhatsApp account is at risk of this social-engineering attack. Our investigation found that there were victims in India, Nigeria, the UK and multiple other locations, demonstrating the attacks' far-reaching impact.
How to prevent an attack
With the increased time spent on smart phones and apps, it is crucial that users remain vigilant to the malicious activities of cyber criminals and scammers. The majority of popular apps, including WhatsApp, offer two-factor authentication (2FA) which provides an extra layer of protection for online accounts.
WhatsApp allows users to set up a unique PIN through their settings. This PIN must be input every time the account wants to use a new phone number or if they detect suspicious activity. Enabling this security feature will prevent the attacker from accessing the account with only the single-use six-digit code.
WhatsApp is increasingly a standard method of communication for employees, including on corporate devices. If your workforce regularly use the platform, make users aware of the risks from this attack and incorporate guidance on multi-factor authentication to increase employee awareness.