All businesses rely on a network of suppliers and partners to deliver products and services. Attackers can exploit weaknesses in these supply chains as part of their campaigns, usually by tampering with software to install malware or exploiting the legitimate access service providers have to the corporate networks of their customers. As supply chains can be large and complex, defending against attacks conducted via third parties can be difficult. However, businesses can prepare to defend against supply chain attacks by implementing risk management processes to understand and control risks.
Who are the attackers?
Supply chain attacks can be conducted by attackers with a range of motivations and objectives. In June 2021, ransomware attackers exploited weaknesses in software used by managed service providers (MSPs), resulting in the reported compromise of over 1,500 MSP downstream customers by a ransomware group. Earlier in the year, the Solarwinds “Orion” IT infrastructure management software was compromised, almost certainly by a nation-state espionage group. The attackers then delivered software updates to victims tainted with malware, allowing them to gain access to multiple government and private industry networks.
Why attack the supply chain?
Attacking the supply chain is not a new concept - attacks have been seen for several years - but it is an approach that has some significant benefits for attackers with the ability to capitalise on large-scale access. By focusing efforts on upstream providers, attackers often gain access to multiple victims. If the attackers have the operational sophistication to exploit this, it can enable access to a large amount of data to steal or encrypt for the purposes of fraud or extortion, or to a large number of systems on which to gain strategic footholds for onwards attacks.
What can businesses do to protect themselves?
Supply chain risk management is not purely a technical pursuit, it is a process that requires a considered approach to managing suppliers. While not all risks can be eliminated, some efforts to tackle issues can reduce the likelihood and impacts of such attacks. The UK National Cyber Security Centre (NCSC) advocates four key activities to help reduce the risks of supply chain attacks: understand the risks, establish control, check your arrangements and continuous improvement. This model builds in several steps which are an excellent basis upon which businesses can develop their supply chain risk programmes in a methodical way.
Cyber due diligence
One of the key ways in which businesses can understand the risks as part of supply chain risk management is to conduct cyber due diligence exercises. We regularly help businesses assess potential risks from suppliers, partners, and potential acquisition targets so that they can implement measures that improve overall security. Our tiered approach to this can include rapid assessments where time is of the essence, or to be proportionate to the extent of the commercial relationship, through to detailed and even enhanced assessments, which take a more forensic approach, including helping businesses plan for long-term and integration issues.
Our cyber due diligence exercises have helped clients spot potential issues before they have been exploited and have informed their decision-making processes when considering new relationships.
To find out more about our cyber due diligence approach, please contact us at MDRCyber@Mishcon.com.
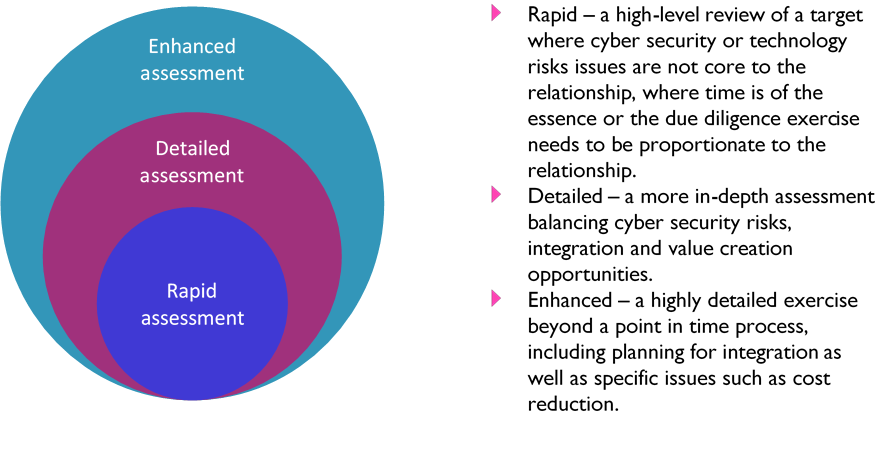
Figure 1 - MDR Cyber's tiered cyber due diligence approach