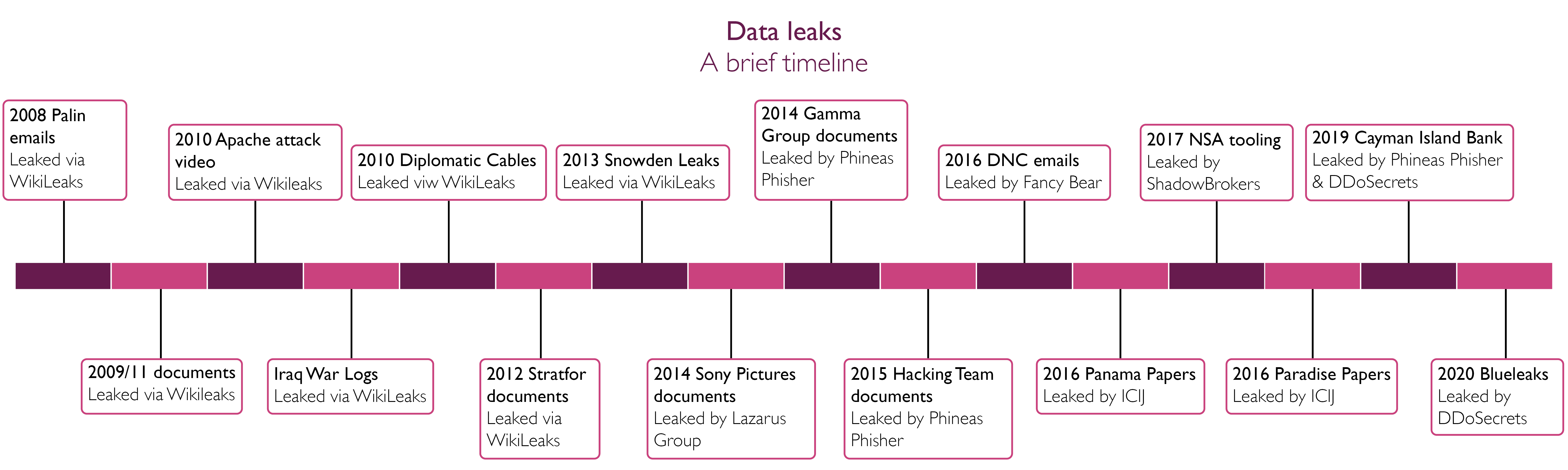
This week we learned of a new large leak of US law enforcement data coined “Blueleaks”. The leak, thought to be from a third-party technology provider, contains police reports, audio and video from over 200 regional and local US police forces throughout the country. As well as revealing policing methods and techniques to the general public, the leak has the potential to seriously embarrass US policing and government, as well as presenting reputational and physical security risks to individuals that can potentially be identified from the tranche.
The leak is the work of the “Distributed Denial of Secrets”, a group of citizen journalists. They have made public hundreds of thousands of files leaked from organisations across the world, leaking data from The Cayman Islands National Bank at the tail end of November in 2019, but also making data available for download from their website. The group position themselves as a direct “competitor” of other leaking organisations, claiming that they have become “deteriorated, poisoned by their various egos and interests”.
The hacking of organisations is viewed by some activists as a means to an end. The leaking of sensitive or non-public information is seen as a way of driving change, putting pressure on politicians and institutions through public exposure.
There is now a professionalisation of these organisations. The International Consortium of Investigative Journalists (ICIJ) who curated and published the Mossack Fonseca “Panama Papers” in 2016 is a credible journalistic source, with public and high-profile members. The latest leaks from US police departments follow this vein, with the members of DDOS Secrets largely having public profiles.
The organisations and individuals involved in leaking are highly divisive. Edward Snowden is viewed by some as a hero and others a traitor, whilst Wikileaks and Julian Assange are seen as journalists and advocates of free speech, or dangerous individuals impacting national security.
Blueleaks is the latest in a long line of online leaking activity. Perhaps the most well-known online leaking channel is Wikileaks, who hit their stride in 2008 with the leaking of Vice Presidential candidate Sarah Palin's emails.
Activism and Hacktivism
In an early seminal leak of 2012, the US “geopolitical intelligence platform” Stratfor was compromised in an ideologically-motivated attack and subsequently five million email messages leaked by Wikileaks. Now held up as a hero among some, Jeremy Hammond was subsequently jailed for his role in this attack and connections with the “Anonymous” hacking collective.
The world has since seen leaks with huge impact on government transparency, such as the Snowden revelations on NSA’s PRISM program in 2013, and impacts on business transparency and personal reputations, such as the Mossack Fonseca leak of the Panamanian law firm from 2016. The global impact of this leak led to resignations of politicians as well as increased scrutiny on many more.
In another ideologically-motivated incident from July 2015, the attacker calling himself “Phineas Fisher” leaked more than a million emails from a compromise of the Italian surveillance malware vendor “Hacking Team”. The communications indicated the firm were in contact with regimes with questionable human rights records and had a huge impact on the firm, whose reputation was severely impacted.
Government leaks
There is a well-trodden path by Nation States in using leaks of sensitive information. Online leaks are now a mainstream tactic – the internet provides a platform that historically was reserved for newspapers and the media. The acceptance of alternative means of news gathering and reporting, as well as the newsworthiness of social media itself, allows leaks of sensitive information to thrive.
A further example is the leaking of documents from the US Democratic National Committee (DNC) in 2016, around the time leading up to the US Presidential elections. In this instance, an online persona calling themselves “Guccifer 2” was the vehicle for the online leaks, although it was widely assessed to be the work of the Russian intelligence services known in the cybersecurity industry as “Fancy Bear”. Although the impact of this is difficult to accurately gauge, the intention of whoever was driving the leaks to meddle in US politics was almost irrefutable.
There is a hypothesis that Nation States may have been involved in some of the larger leaks of offshore data. Similarly, some have questioned the origins and intentions of other leaks by online personas claiming to be hacktivists, but clearly supporting the objectives of Nation States.
In 2017, various US intelligence cyber attack tools were leaked by a group calling themselves the “Shadowbrokers”. One of these in particular was then used in the separate but now infamous “Wannacry” ransomware attacks which crippled multiple businesses and had a huge global impact.
Cybercriminal use of leaks
The impact of publicising private information creates a powerful incentive not just suited to governments or activists -criminals too have used the power of information to their advantage. The Maze ransomware group deliberately uses leaks of data to encourage targets to pay a ransom, not just retrieving access to their data but for it not to be published.
Assessing risks
Many cyber security professionals are used to minimising the threat from investigative journalists, as they were viewed as not posing the risk that other threats did. The use of the media to publicise the results of successful attacks, or to provide insiders with a mechanism to reach a mass market, changes the dynamic.
Our working hypothesis is that the level of sensitivity of the data is not the main determiner of the risk posed when looking at these issues. More sensitive data of course is more risky, however within that category it is useful to understand the impact that leaks have had or may have. Looking at the data through the lens of who could be persuaded to publish it and who can gain access provides an additional level of depth to an assessment.
When assessing the risks to internal data, the media and citizen or activist journalists should be looked on as magnifying the impact of other attacks, if the data being assessed would be sensational or media-worthy.
We believe that threat groups who target this data are interested in their own citizens' data held abroad. This could include for example relating to offshore assets, wealth of the location of individuals whom are targets themselves.
| |
Attacker or Insider |
| High Ability or Access |
Low Ability or Access |
| Publishing or Platform |
Curated or Managed
|
Highest impact leaks e.g. DNC or ICIJ |
Medium impact leaks e.g. journalistic reporting
|
| Indiscriminate or Niche |
High impact leaks e.g. Wikileaks or Stratfor |
Lower impact leaks e.g. Anonymous or Maze |
Our working model for these types of risks is set out above. We assess the level to which data could be published, the reach of the platform and whether it will be journalistically curated for maximum effect. We also look at the threat posed by an attacker or insider from those who have privileged or widescale access to entire data set, or the ability to package data up and disseminate it more widely. For example the Fancy Bears leaks approached journalists and Wikileaks directly, essentially targeted a mainstream audience. This is in contrast with the Maze ransomware group who publishes data on the Dark Web, which often doesn’t generate mainstream headlines.
The level of risk for an organisation is not fixed and can change quickly depending on external factors. The risk profile of organsations that supplied to the US ICE changed with the introduction of new policies by the current administration, and the recent Black Lives Matter protests have focused attention on US law enforcement. Whilst continuous risk assessment is well known concept, it is often not implemented in practice.
Incident Response for Data Leakage
In our experience responding to a data leakage event which results in data publication creates additional challenges for conducting incident response. Response teams face greater time pressure while simultaneously supporting communications teams in engaging an evolving narrative in real time, rather than releasing conducting co-ordinated disclosure following the completion of an investigation.
Data leaks are not just a technical issue to respond to. During a client project we identified a range of risk scenarios related to the publication of sensitive data. These ranged from a senior staff member's inbox being compromised through to leaks of entire document collaboration tools. The risks and responses to these data sources were all different and required specific incident response plans bringing in teams from across the organisation.
We recommend that communications, marketing and legal teams are engaged as early as possible if publication is likely. When information is sensitive, covered by legal privilege or may be damaging court orders can prevent some publication. Framing the issue appropriately is also key, as often publication looks to support a specific agenda.
The future of leaks
There is no doubt that leaked information will continue to make headlines, and therefore will be a target. The data from Mossack Fonseca, if taken in paper form, would have filled a large shipping container in our estimation, bringing to life how the digital world has magnified these issues. Whilst the volume of these attacks has decreased in recent years their impact remains substantial.
If your organisation holds data that may be sensitive, or relates to wealth, taxation or topics that are in the media there may be greater exposures than appear on the surface. We recommend assessing the risks associated with this model and how your response would manage them.